AZ-104: Microsoft Azure Administrator
You have an Azure subscription that contains a virtual network named VNET1. VNET1 contains the subnets shown in the following table.
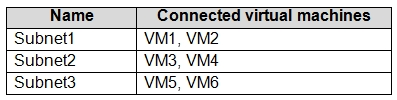
Each virtual machine uses a static IP address.
You need to create network security groups (NSGs) to meet following requirements:
- Allow web requests from the internet to VM3, VM4, VM5, and VM6.
- Allow all connections between VM1 and VM2.
- Allow Remote Desktop connections to VM1.
- Prevent all other network traffic to VNET1.
What is the minimum number of NSGs you should create?
1
3
4
12
Answer is 1
NSGs can be associated to subnets, individual VMs (classic), or individual network interfaces (NIC) attached to VMs (Resource Manager). You can associate zero, or one, NSG(s) to each VNet subnet and NIC in a virtual machine. The same NSG can be associated to as many subnets and NICs as you choose.
So, you can create 1 NSG and associate it with all 3 Subnets.
- Allow web requests from internet to VM3, VM4, VM5 and VM 6: You need to add an inbound rule to allow Internet TCP 80 to VM3, VM4, VM5 and VM6 static IP addresses.
- Allow all connections between VM1 & VM2: You do not need an NSG as communication in the same VNet is allowed by default, without even configuring NSG.
- Allow remote desktop to VM1: You need to add an inbound rule to allow RDP 3389 in VM1’s static IP address.
- Prevent all other network traffic to VNET1: You do not need to configure any NSG as the there is explicit deny rule (DenyAllInbound) in every NSG.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-network/security-overview#default-security-rules
You have an Azure subscription that contains the resources in the following table.
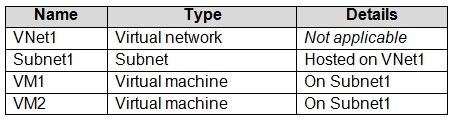
VM1 and VM2 are deployed from the same template and host line-of-business applications.
You configure the network security group (NSG) shown in the exhibit.
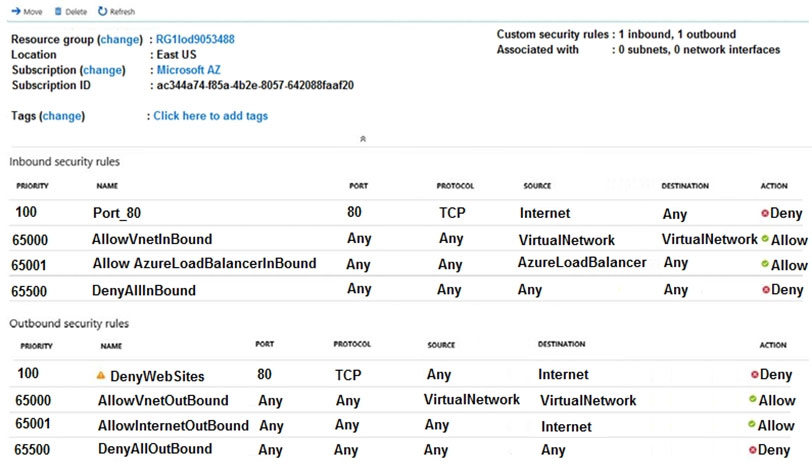
You need to prevent users of VM1 and VM2 from accessing websites on the Internet over TCP port 80.
What should you do?
Disassociate the NSG from a network interface
Change the Port_80 inbound security rule.
Associate the NSG to Subnet1.
Change the DenyWebSites outbound security rule.
Answer is Associate the NSG to Subnet1.
Outbound rule “DenyWebSites” is setup correctly to block outbound internet traffic over port 80. In the screenshot it states, "Associated with: 0 subnets, 0 NIC's", so you need to associate the NSG to Subnet1.You can associate or dissociate a network security group from a NIC or Subnet.
You can associate or dissociate a network security group from a network interface or subnet.
The NSG has the appropriate rule to block users from accessing the Internet. We just need to associate it with Subnet1.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-network/manage-network-security-group
You have the Azure virtual machines shown in the following table.

A DNS service is installed on VM1.
You configure the DNS servers settings for each virtual network as shown in the following exhibit.
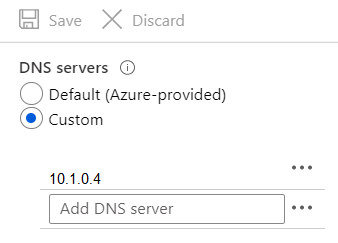
You need to ensure that all the virtual machines can resolve DNS names by using the DNS service on VM1.
What should you do?
Configure a conditional forwarder on VM1
Add service endpoints on VNET1
Add service endpoints on VNET2 and VNET3
Configure peering between VNET1, VNET2, and VNET3
Answer is Configure peering between VNET1, VNET2, and VNET3
Use Virtual network peering to connect virtual networks to be able to connect to other VMs in different VNETs. Virtual network peering enables you to seamlessly connect networks in Azure Virtual Network. The virtual networks appear as one for connectivity purposes. The traffic between virtual machines uses the Microsoft backbone infrastructure.
B, C: Virtual Network (VNet) service endpoint provides secure and direct connectivity to Azure services over an optimized route over the Azure backbone network. Endpoints allow you to secure your critical Azure service resources to only your virtual networks. Service Endpoints enables private IP addresses in the VNet to reach the endpoint of an Azure service without needing a public IP address on the VNet.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-network/virtual-network-service-endpoints-overview
https://docs.microsoft.com/en-us/azure/virtual-network/virtual-network-peering-overview
You have an Azure subscription named Subscription1 that contains an Azure virtual network named VNet1. VNet1 connects to your on-premises network by using Azure ExpressRoute.
You plan to prepare the environment for automatic failover in case of ExpressRoute failure.
You need to connect VNet1 to the on-premises network by using a site-to-site VPN. The solution must minimize cost.
Which three actions should you perform?
Create a connection
Create a local site VPN gateway
Create a VPN gateway that uses the VpnGw1 SKU
Create a gateway subnet
Create a VPN gateway that uses the Basic SKU
Answer is A-B-C
For a site to site VPN, you need:
- a local gateway
- a gateway subnet
- a VPN gateway
- a connection to connect the local gateway and the VPN gateway
However, the question states that VNet1 connects to your on-premises network by using Azure ExpressRoute. For an ExpressRoute connection, VNET1 must already be configured with a gateway subnet so we don't need another one.
Note: BasicSKU cannot coexist with ExpressRoute. You must use a non-Basic SKU gateway for both the ExpressRoute gateway and the VPN gateway.
Reference:
https://docs.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-howto-site-to-site-resource-manager-portal
https://azure.microsoft.com/es-es/pricing/details/vpn-gateway
You have an Azure virtual machine named VM1 that connects to a virtual network named VNet1. VM1 has the following configurations:
- Subnet: 10.0.0.0/24
- Availability set: AVSet
- Network security group (NSG): None
- Private IP address: 10.0.0.4 (dynamic)
- Public IP address: 40.90.219.6 (dynamic)
You deploy a standard, Internet-facing load balancer named slb1.
You need to configure slb1 to allow connectivity to VM1.
Which changes should you apply to VM1 as you configure slb1?
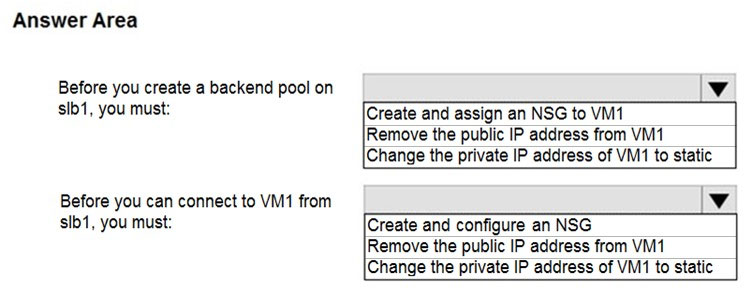
Box 1: Remove the public IP address from VM1
Note: A public load balancer can provide outbound connections for virtual machines (VMs) inside your virtual network. These connections are accomplished by translating their private IP addresses to public IP addresses. Public Load Balancers are used to load balance internet traffic to your VMs. Load balancer and the public IP address SKU must match when you use them with public IP addresses. Only Basic SKU IPs work with the Basic SKU load balancer and only Standard SKU IPs work with Standard SKU load balancers.
Box 2: Create and configure an NSG
NSGs are used to explicitly permit allowed traffic. If you do not have an NSG on a subnet or NIC of your virtual machine resource, traffic is not allowed to reach this resource.
Note: You can only attach virtual machines that are in the same location and on the same virtual network as the LB. Also, when adding them to a backend pool, it doesn’t matter in which status are the VMs.
Reference:
https://docs.microsoft.com/en-us/azure/aks/load-balancer-standard
https://docs.microsoft.com/en-us/azure/virtual-network/public-ip-addresses
https://stackoverflow.com/questions/52882024/cannot-add-vm-to-standard-azure-load-balancer
https://docs.microsoft.com/en-us/azure/load-balancer/skus
https://docs.microsoft.com/en-us/azure/load-balancer/backend-pool-management
You plan to use Azure Network Watcher to perform the following tasks:
- Task1: Identify a security rule that prevents a network packet from reaching an Azure virtual machine.
- Task2: Validate outbound connectivity from an Azure virtual machine to an external host.
Which feature should you use for each task?
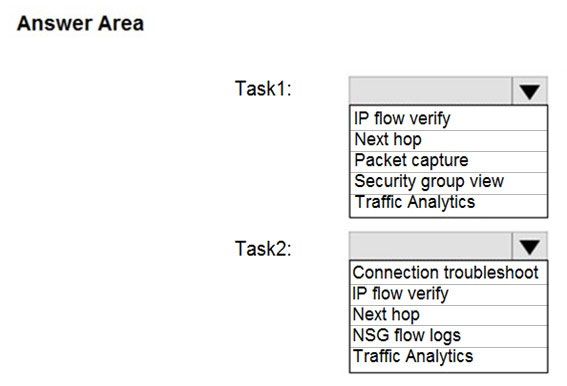
Box 1: IP flow verify
At some point, a VM may become unable to communicate with other resources, because of a security rule. The IP flow verify capability enables you to specify a source and destination IPv4 address, port, protocol (TCP or UDP), and traffic direction (inbound or outbound). IP flow verify then tests the communication and informs you if the connection succeeds or fails. If the connection fails, IP flow verify tells you which.
Box 2: Connection troubleshoot
Diagnose outbound connections from a VM: The connection troubleshoot capability enables you to test a connection between a VM and another VM, an FQDN, a URI, or an IPv4 address. The test returns similar information returned when using the connection monitor capability, but tests the connection at a point in time, rather than monitoring it over time, as connection monitor does. Learn more about how to troubleshoot connections using connection-troubleshoot.
Reference:
https://docs.microsoft.com/en-us/azure/network-watcher/network-watcher-monitoring-overview
You have an Azure virtual machine named VM1.
The network interface for VM1 is configured as shown in the exhibit.
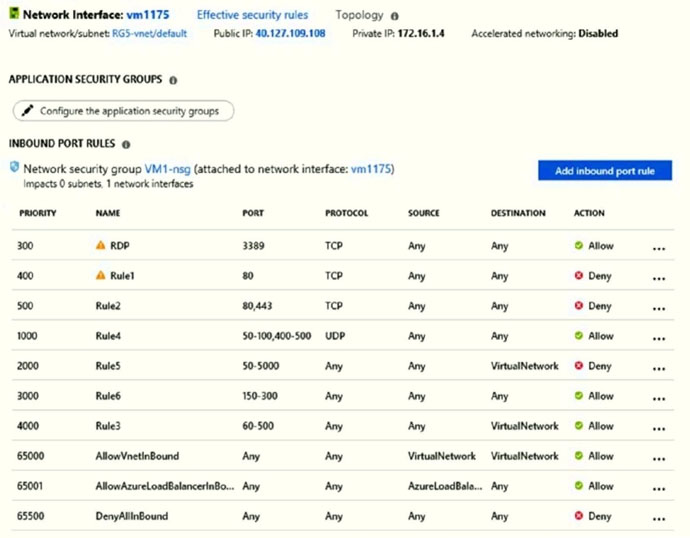
You deploy a web server on VM1, and then create a secure website that is accessible by using the HTTPS protocol. VM1 is used as a web server only.
You need to ensure that users can connect to the website from the Internet.
What should you do?
Modify the protocol of Rule4
Delete Rule1
For Rule5, change the Action to Allow and change the priority to 401
Create a new inbound rule that allows TCP protocol 443 and configure the rule to have a priority of 501.
Answer is For Rule5, change the Action to Allow and change the priority to 401
HTTPS uses port 443.
Rule2, with priority 500, denies HTTPS traffic.
Rule5, with priority changed from 2000 to 401, would allow HTTPS traffic.
Note: Priority is a number between 100 and 4096. Rules are processed in priority order, with lower numbers processed before higher numbers, because lower numbers have higher priority. Once traffic matches a rule, processing stops. As a result, any rules that exist with lower priorities (higher numbers) that have the same attributes as rules with higher priorities are not processed.
Note: There are several versions of this question in the exam.
The question has two possible correct answers:
1. Change the priority of Rule3 to 450.
2. For Rule5, change the Action to Allow and change the priority to 401.
Other incorrect answer options you may see on the exam include the following:
- Modify the action of Rule1.
- Change the priority of Rule6 to 100.
- For Rule4, change the protocol from UDP to Any.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-network/network-security-groups-overview
You create an Azure Storage account named contosostorage.
You plan to create a file share named data.
Users need to map a drive to the data file share from home computers that run Windows 10.
Which outbound port should you open between the home computers and the data file share?
80
443
445
3389
Answer is 445
Port 445 is used for SMB (Server Message Block) protocol, which is what Windows uses for file sharing. Note that some ISPs block this port, so if you experience issues, a VPN or Azure ExpressRoute connection may be necessary to allow the traffic. Always ensure you are following security best practices when opening ports, especially when dealing with potentially sensitive data.
Incorrect:
Port 80: HTTP, this is for web
Port 443: HTTPS, for web too
Port 3389: Remote desktop protocol (RDP)
Reference:
https://learn.microsoft.com/en-us/azure/storage/files/storage-how-to-use-files-windows#prerequisites
You have an Azure policy as shown in the following exhibit:
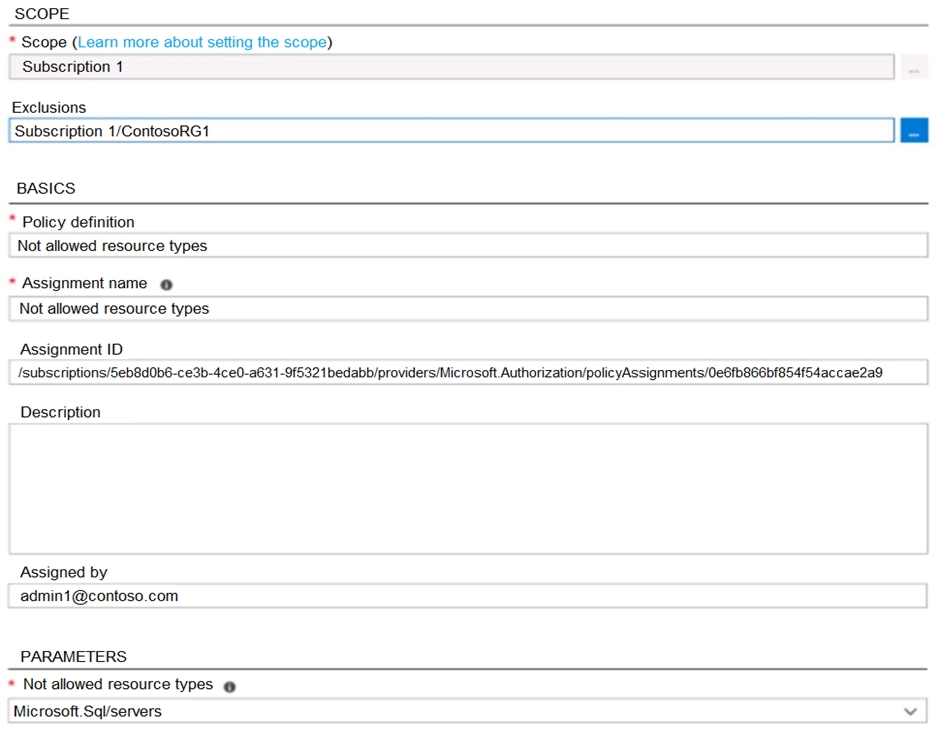
What is the effect of the policy?
You are prevented from creating Azure SQL servers anywhere in Subscription 1.
You can create Azure SQL servers in ContosoRG1 only.
You are prevented from creating Azure SQL Servers in ContosoRG1 only.
You can create Azure SQL servers in any resource group within Subscription 1.
Answer is You can create Azure SQL servers in ContosoRG1 only.
You are prevented from creating Azure SQL servers anywhere in Subscription 1, except from ContosoRG1. There’s an Exclusion on ContosoRG1.
Not allowed resource types (Deny): Prevents a list of resource types from being deployed.
Reference:
https://docs.microsoft.com/en-us/azure/governance/policy/overview#policy-definition
You have an on-premises server that contains a folder named D:Folder1.
You need to copy the contents of D:Folder1 to the public container in an Azure Storage account named contosodata.
Which command should you run?
https://contosodata.blob.core.windows.net/public
azcopy sync D:folder1 https://contosodata.blob.core.windows.net/public --snapshot
azcopy copy D:folder1 https://contosodata.blob.core.windows.net/public --recursive
az storage blob copy start-batch D:Folder1 https://contosodata.blob.core.windows.net/public
Answer is azcopy copy D:folder1 https://contosodata.blob.core.windows.net/public --recursive
The azcopy copy command copies a directory (and all of the files in that directory) to a blob container. The result is a directory in the container by the same name.
Incorrect Answers:
B: The azcopy sync command replicates the source location to the destination location. However, the file is skipped if the last modified time in the destination is more recent.
D: The az storage blob copy start-batch command copies multiple blobs to a blob container.
Reference:
https://docs.microsoft.com/en-us/azure/storage/common/storage-use-azcopy-blobs
https://docs.microsoft.com/en-us/azure/storage/common/storage-ref-azcopy-copy