AZ-104: Microsoft Azure Administrator
You have an Azure subscription that contains the resources shown in the following table.
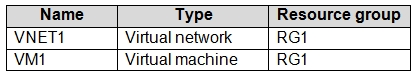
The Not allowed resource types Azure policy is assigned to RG1 and uses the following parameters:
Microsoft.Network/virtualNetworks
Microsoft.Compute/virtualMachines
In RG1, you need to create a new virtual machine named VM2, and then connect VM2 to VNET1.
What should you do first?
Remove Microsoft.Compute/virtualMachines from the policy.
Create an Azure Resource Manager template
Add a subnet to VNET1.
Remove Microsoft.Network/virtualNetworks from the policy.
Answer is Remove Microsoft.Compute/virtualMachines from the policy.
The Not allowed resource types Azure policy prohibits the deployment of specified resource types. You specify an array of the resource types to block.
Virtual Networks and Virtual Machines are prohibited.
By removing VMs from policy you will be able to create a new VM on the RG, and assign an already existing Vnet to the VM.
Reference:
https://docs.microsoft.com/en-us/azure/governance/policy/samples/not-allowed-resource-types
Your company has an Azure subscription named Subscription1.
The company also has two on-premises servers named Server1 and Server2 that run Windows Server 2016. Server1 is configured as a DNS server that has a primary DNS zone named adatum.com. Adatum.com contains 1,000 DNS records.
You manage Server1 and Subscription1 from Server2. Server2 has the following tools installed:
- The DNS Manager console
- Azure PowerShell
- Azure CLI 2.0
You need to move the adatum.com zone to an Azure DNS zone in Subscription1. The solution must minimize administrative effort.
What should you use?
Azure CLI
Azure PowerShell
the Azure portal
the DNS Manager console
Answer is Azure CLI
Azure DNS supports importing and exporting zone files by using the Azure command-line interface (CLI). Zone file import is not currently supported via Azure PowerShell or the Azure portal.
PrivateDNSMigrationScript is for migrating legacy Azure DNS private zones to the new Azure DNS private zone resource.
Reference:
https://docs.microsoft.com/en-us/azure/dns/dns-import-export https://docs.microsoft.com/en-us/azure/dns/private-dns-migration-guide
You have a public load balancer that balances ports 80 and 443 across three virtual machines.
You need to direct all the Remote Desktop Protocol (RDP) connections to VM3 only.
What should you configure?
an inbound NAT rule
a new public load balancer for VM3
a frontend IP configuration
a load balancing rule
Answer is an inbound NAT rule
Create an Inbound NAT rule in the LB front end to port forward 3389 to VM3.
Create a load balancer inbound network address translation (NAT) rule to forward traffic from a specific port of the front-end IP address to a specific port of a back-end VM.
Reference:
https://docs.microsoft.com/en-us/azure/load-balancer/tutorial-load-balancer-port-forwarding-portal
You have an Azure virtual machine that runs Windows Server 2019 and has the following configurations:
- Name: VM1
- Location: West US
- Connected to: VNET1
- Private IP address: 10.1.0.4
- Public IP addresses: 52.186.85.63
- DNS suffix in Windows Server: Adatum.com
You create the Azure DNS zones shown in the following table.
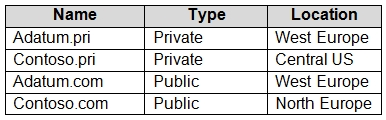
You need to identify which DNS zones you can link to VNET1 and the DNS zones to which VM1 can automatically register.
Which zones should you identify?

Box 1: The private zones only
Box 2: The private zones only
You can only link VNETs to private DNS zones only and accordingly auto register a VNET only to a private DNS zones. Private DNS zones can be linked with VNETs (not public ones). And VM can auto-register to any private DNS zone linked with the Vnet and with auto-registration option set. To resolve the records of a private DNS zone from your virtual network, you must link the virtual network with the zone. Linked virtual networks have full access and can resolve all DNS records published in the private zone.
Reference:
https://docs.microsoft.com/en-us/azure/dns/private-dns-overview
You plan to create an Azure virtual machine named VM1 that will be configured as shown in the following exhibit.
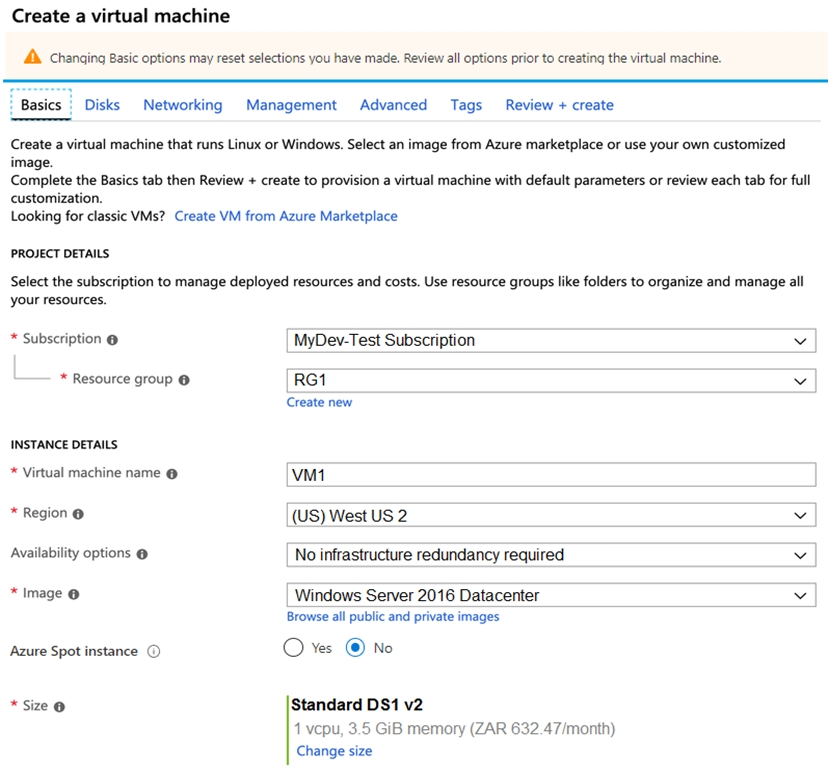
The planned disk configurations for VM1 are shown in the following exhibit.
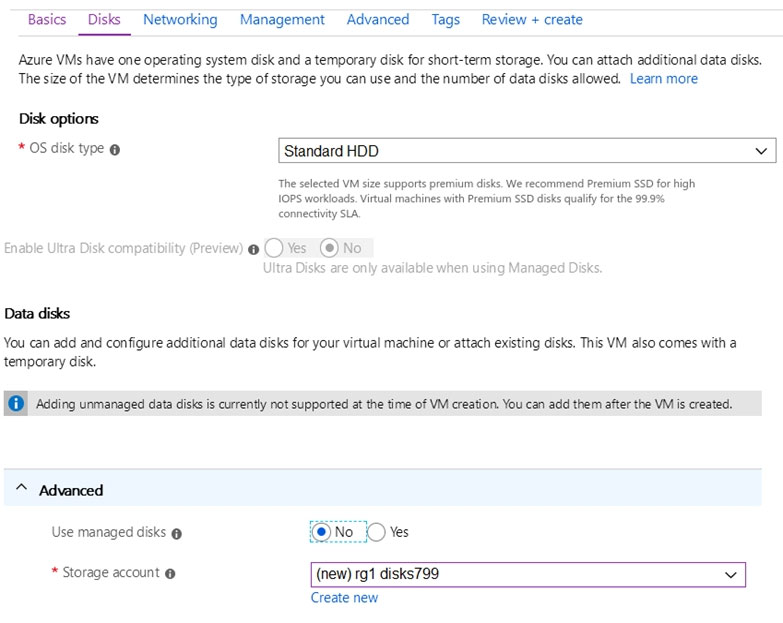
You need to ensure that VM1 can be created in an Availability Zone.
Which two settings should you modify?
Use managed disks
OS disk type
Availability options
Size
Image
Answer is A & C
A: Your VMs should use managed disks if you want to move them to an Availability Zone by using Site Recovery.
C: When you create a VM for an Availability Zone, Under Settings > High availability, select one of the numbered zones from the Availability zone dropdown.
Reference:
https://docs.microsoft.com/en-us/azure/site-recovery/move-azure-vms-avset-azone
https://docs.microsoft.com/en-us/azure/virtual-machines/windows/create-portal-availability-zone
https://docs.microsoft.com/en-us/azure/virtual-machines/manage-availability
https://docs.microsoft.com/en-us/azure/availability-zones/az-overview#availability-zones
You have the Azure virtual network named VNet1 that contains a subnet named Subnet1. Subnet1 contains three Azure virtual machines. Each virtual machine has a public IP address.
The virtual machines host several applications that are accessible over port 443 to users on the Internet.
Your on-premises network has a site-to-site VPN connection to VNet1.
You discover that the virtual machines can be accessed by using the Remote Desktop Protocol (RDP) from the Internet and from the on-premises network.
You need to prevent RDP access to the virtual machines from the Internet, unless the RDP connection is established from the on-premises network. The solution must ensure that all the applications can still be accessed by the Internet users.
What should you do?
Modify the address space of the local network gateway
Create a deny rule in a network security group (NSG) that is linked to Subnet1
Remove the public IP addresses from the virtual machines
Modify the address space of Subnet1
Answer is Create a deny rule in a network security group (NSG) that is linked to Subnet1
You can use a site-to-site VPN to connect your on-premises network to an Azure virtual network. Users on your on-premises network connect by using the RDP or SSH protocol over the site-to-site VPN connection. You have to deny direct RDP or SSH access over the internet through an NSG.
Reference:
https://docs.microsoft.com/en-us/azure/security/fundamentals/network-best-practices
You have Azure virtual machines that run Windows Server 2019 and are configured as shown in the following table.
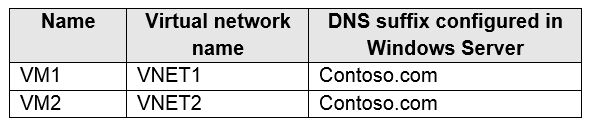
You create a public Azure DNS zone named adatum.com and a private Azure DNS zone named contoso.com.
For controso.com, you create a virtual network link named link1 as shown in the exhibit.

You discover that VM1 can resolve names in contoso.com but cannot resolve names in adatum.com. VM1 can resolve other hosts on the Internet.
You need to ensure that VM1 can resolve host names in adatum.com.
What should you do?
Update the DNS suffix on VM1 to be adatum.com
Configure the name servers for adatum.com at the domain registrar
Create an SRV record in the contoso.com zone
Modify the Access control (IAM) settings for link1
Answer is Configure the name servers for adatum.com at the domain registrar
Adatum.com is a public DNS zone. The Internet top level domain DNS servers need to know which DNS servers to direct DNS queries for adatum.com to. You configure this by configuring the name servers for adatum.com at the domain registrar.
Wrong answers;
A. This would change the domain suffix of VM1 which is useless.
C. SRV records tie a host/IP to a service.
D. Link1 is only for contoso.com and would help our case.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-network/virtual-networks-name-resolution-for-vms-and-role-instances
You have an Azure subscription.
Users access the resources in the subscription from either home or from customer sites. From home, users must establish a point-to-site VPN to access the Azure resources. The users on the customer sites access the Azure resources by using site-to-site VPNs.
You have a line-of-business-app named App1 that runs on several Azure virtual machine. The virtual machines run Windows Server 2016.
You need to ensure that the connections to App1 are spread across all the virtual machines.
What are two possible Azure services that you can use?
an internal load balancer
a public load balancer
an Azure Content Delivery Network (CDN)
Traffic Manager
an Azure Application Gateway
Answer is A & E
Network traffic from the VPN gateway is routed to the cloud application through an internal load balancer. The load balancer is located in the front-end subnet of the application.
A: The customer sites are connected through VPNs, so an internal load balancer is enough.
B: The customer sites are connected through VPNs, so there's no need for a public load balancer, an internal load balancer is enough.
C: A CDN does not provide load balancing for applications, so it not relevant for this situation.
D: Traffic manager is a DNS based solution to direct users' requests to the nearest (typically) instance and does not provide load balancing for this situation.
E: Azure Application Gateway is a valid option, as it provides load balancing in addition to routing and security functions
Reference:
https://docs.microsoft.com/en-us/azure/architecture/reference-architectures/hybrid-networking/vpn
https://docs.microsoft.com/en-us/azure/load-balancer/load-balancer-overview
https://docs.microsoft.com/en-us/azure/application-gateway/overview
You have an Azure DNS zone named adatum.com.
You need to delegate a subdomain named research.adatum.com to a different DNS server in Azure.
What should you do?
Create an NS record named research in the adatum.com zone.
Create an PTR record named research in the adatum.com zone.
Modify the SOA record of adatum.com.
Create an A record named *.research in the adatum.com zone.
Answer is Create an NS record named research in the adatum.com zone.
An NS record or (name server record) tells recursive name servers which name servers are authoritative for a zone. You can have as many NS records as you would like in your zone file. The benefit of having multiple NS records is the redundancy of your DNS service.
You need to create a name server (NS) record for the zone.
Reference:
https://docs.microsoft.com/en-us/azure/dns/delegate-subdomain
You deploy an Azure Kubernetes Service (AKS) cluster named Cluster1 that uses the IP addresses shown in the following table.
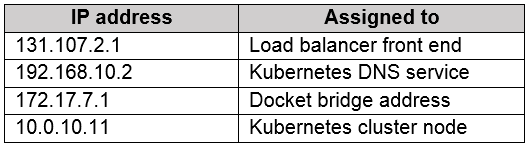
You need to provide internet users with access to the applications that run in Cluster1.
Which IP address should you include in the DNS record for Cluster1?
131.107.2.1
10.0.10.11
172.17.7.1
192.168.10.2
Answer is 131.107.2.1
To be able to access applications on Kubernetes, you need an application Load Balancer created by Azure which have public IP.
Note: 10.X.X.X range is private.
Reference:
https://docs.microsoft.com/en-us/azure/aks/load-balancer-standard