AZ-104: Microsoft Azure Administrator
You have an Azure subscription named Subscription1 that has the following providers registered:
- Authorization
- Automation
- Resources
- Compute
- KeyVault
- Network
- Storage
- Billing
- Web
Subscription1 contains an Azure virtual machine named VM1 that has the following configurations:
- Private IP address: 10.0.0.4 (dynamic)
- Network security group (NSG): NSG1
- Public IP address: None
- Availability set: AVSet
- Subnet: 10.0.0.0/24
- Managed disks: No
Location: East US
You need to record all the successful and failed connection attempts to VM1.
Which three actions should you perform?
Enable Azure Network Watcher in the East US Azure region.
Add an Azure Network Watcher connection monitor.
Register the MicrosoftLogAnalytics provider.
Create an Azure Storage account.
Register the Microsoft.Insights resource provider.
Enable Azure Network Watcher flow logs.
Answer is A - E - F
A network security group (NSG) enables you to filter inbound traffic to, and outbound traffic from, a virtual machine (VM). You can log network traffic that flows through an NSG with Network Watcher's NSG flow log capability.
1. Create a VM with a network security group
2. Enable Network Watcher and register the Microsoft.Insights provider
3. Enable a traffic flow log for an NSG, using Network Watcher's NSG flow log capability
4. Download logged data
5. View logged data
Note: Storage account is already created since VMs have unmanaged disks.
Reference:
https://docs.microsoft.com/en-us/azure/network-watcher/network-watcher-nsg-flow-logging-portal
https://docs.microsoft.com/en-us/answers/questions/3619/what-is-the-difference-between-managed-disk-and-un.html
You have an Azure subscription named Subscription1. Subscription1 contains a virtual machine named VM1.
You install and configure a web server and a DNS server on VM1.
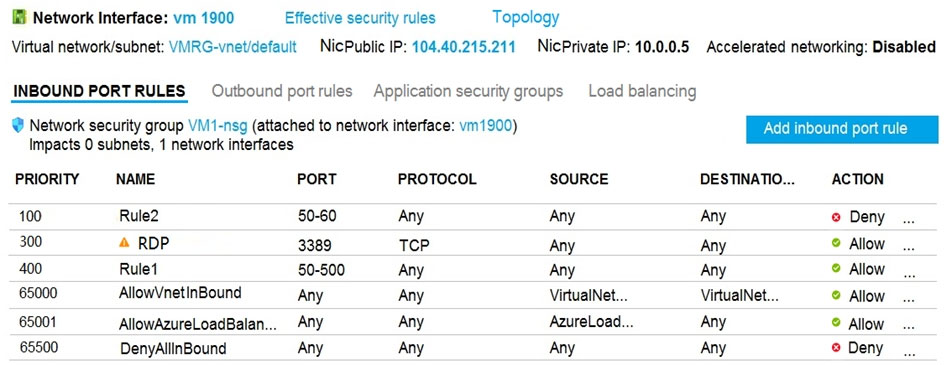
VM1 has the effective network security rules shown in the following exhibit:
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
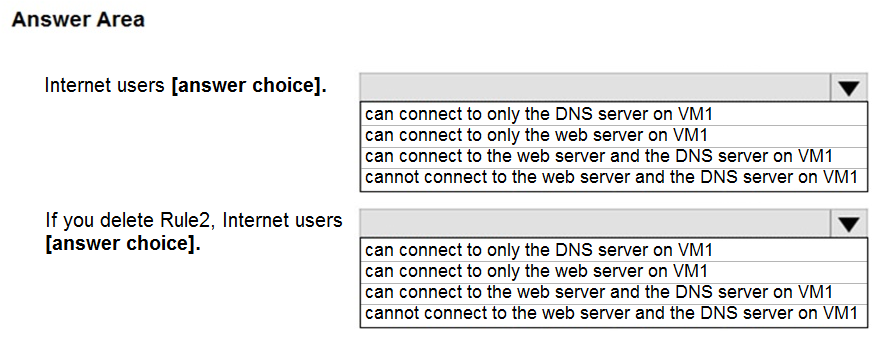
Box 1: B
Rule2 blocks ports 50-60, which includes port 53, the DNS port. Internet users can reach to the Web server, since it uses port 80.
Box 2: C
If Rule2 is removed internet users can reach the DNS server as well.
Note: Rules are processed in priority order, with lower numbers processed before higher numbers, because lower numbers have higher priority. Once traffic matches a rule, processing stops. As a result, any rules that exist with lower priorities (higher numbers) that have the same attributes as rules with higher priorities are not processed.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-network/security-overview
You plan to deploy several Azure virtual machines that will run Windows Server 2019 in a virtual machine scale set by using an Azure Resource Manager template.
You need to ensure that NGINX is available on all the virtual machines after they are deployed.
What should you use?
Deployment Center in Azure App Service
A Desired State Configuration (DSC) extension
the New-AzConfigurationAssignment cmdlet
a Microsoft Intune device configuration profile
Answer is A Desired State Configuration (DSC) extension
Azure virtual machine extensions are small packages that run post-deployment configuration and automation on Azure virtual machines.
In the following example, the Azure CLI is used to deploy a custom script extension to an existing virtual machine, which installs a Nginx webserver.
az vm extension set
--resource-group myResourceGroup
--vm-name myVM --name customScript
--publisher Microsoft.Azure.Extensions
--settings '{"commandToExecute": "apt-get install -y nginx"}
Note:
There are several versions of this question in the exam. The question has two correct answers:
1. a Desired State Configuration (DSC) extension
2. Azure Custom Script Extension
The question can have other incorrect answer options, including the following:
- the Publish-AzVMDscConfiguration cmdlet
- Azure Application Insights
Reference:
https://docs.microsoft.com/en-us/azure/architecture/framework/devops/automation-configuration
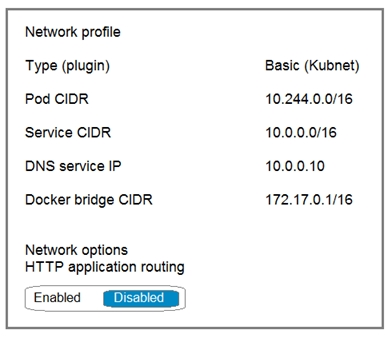
You deploy an Azure Kubernetes Service (AKS) cluster that has the network profile shown in the following exhibit.
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
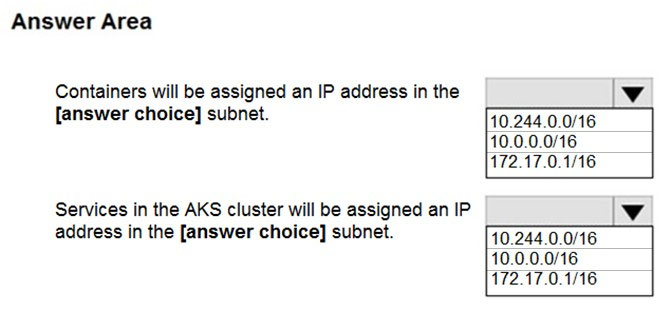
Box 1: 10.244.0.0/16
The Pod CIDR, because containers live inside Pods.
Note: You can't change this address range once the cluster is deployed, if you need more addresses for additional nodes.
Box 2: 10.0.0.0/16
The Service CIDR is used to assign internal services in the AKS cluster an IP address.
Reference:
https://docs.microsoft.com/en-us/azure/aks/configure-kubenet
https://docs.microsoft.com/en-us/azure/aks/configure-azure-cni#plan-ip-addressing-for-your-cluster
You have an Azure subscription that contains a virtual network named VNet1. VNet1 uses an IP address space of 10.0.0.0/16 and contains the subnets in the following table:
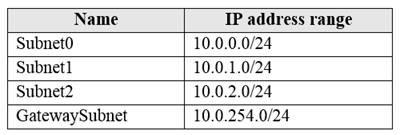
Subnet1 contains a virtual appliance named VM1 that operates as a router.
You create a routing table named RT1.
You need to route all inbound traffic from the VPN gateway to VNet1 through VM1.
How should you configure RT1?
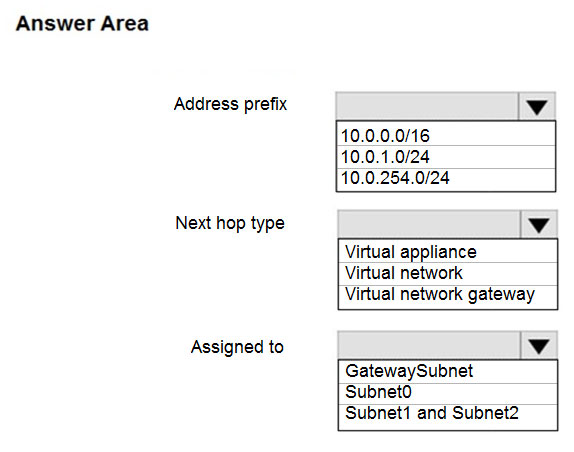
Box 1: 10.0.0.0/16
Address prefix
destination-> Vnet 1 (Address space of Vnet1)
Box 2: Virtual appliance
Next hop type
VM1 ->Virtual Appliance. You can specify IP address of VM 1 when configuring next hop as Virtual appliance.
Box 3: Gateway Subnet
Assigned to
This route is to be followed by Gateway Subnet for the incoming traffic. You can associate routing table to the Subnet from Rout Table -> subnet ->Associate.
You have five Azure virtual machines that run Windows Server 2016. The virtual machines are configured as web servers.
You have an Azure load balancer named LB1 that provides load balancing services for the virtual machines.
You need to ensure that visitors are serviced by the same web server for each request.
What should you configure?
Floating IP (direct server return) to Enabled
Floating IP (direct server return) to Disabled
a health probe
Session persistence to Client IP and Protocol
Answer is Session persistence to Client IP and Protocol
With Sticky Sessions when a client starts a session on one of your web servers, session stays on that specific server. To configure An Azure Load-Balancer for Sticky Sessions set Session persistence to Client IP.
Note:
There are several versions of this question in the exam. The question can have other incorrect answer options, including the following:
1. Idle Time-out (minutes) to 20
2. Protocol to UDP
Reference:
https://cloudopszone.com/configure-azure-load-balancer-for-sticky-sessions/
Your on-premises network contains an SMB share named Share1.
You have an Azure subscription that contains the following resources:
- A web app named webapp1
- A virtual network named VNET1
You need to ensure that webapp1 can connect to Share1.
What should you deploy?
an Azure Application Gateway
an Azure Active Directory (Azure AD) Application Proxy
an Azure Virtual Network Gateway
Answer is an Azure Virtual Network Gateway
A Site-to-Site VPN gateway connection can be used to connect your on-premises network to an Azure virtual network over an IPsec/IKE (IKEv1 or IKEv2) VPN tunnel. This type of connection requires a VPN device, a VPN gateway, located on-premises that has an externally facing public IP address assigned to it.
A: Application Gateway is for http, https and Websocket - Not SMB
B: Application Proxy is also for accessing web applications on-prem - Not SMB. Application Proxy is a feature of Azure AD that enables users to access on-premises web applications from a remote client.
Reference:
https://docs.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-howto-site-to-site-resource-manager-portal
You have an Azure subscription named Sub1.
You plan to deploy a multi-tiered application that will contain the tiers shown in the following table.

You need to recommend a networking solution to meet the following requirements:
- Ensure that communication between the web servers and the business logic tier spreads equally across the virtual machines.
- Protect the web servers from SQL injection attacks.
Which Azure resource should you recommend for each requirement?
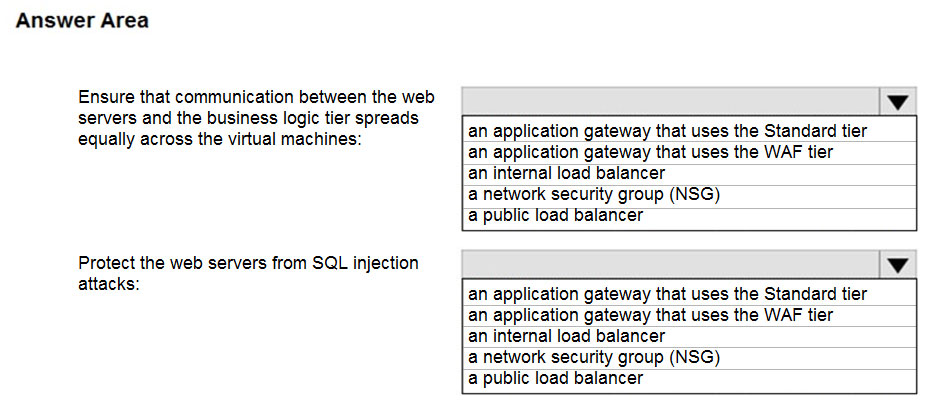
Box 1: an internal load balancer
Azure Internal Load Balancer (ILB) provides network load balancing between virtual machines that reside inside a cloud service or a virtual network with a regional scope.
Box 2: an application gateway that uses the WAF tier
Azure Web Application Firewall (WAF) on Azure Application Gateway provides centralized protection of your web applications from common exploits and vulnerabilities. Web applications are increasingly targeted by malicious attacks that exploit commonly known vulnerabilities. Application gateway which uses WAF tier.
Reference:
https://docs.microsoft.com/en-us/azure/web-application-firewall/ag/ag-overview
You plan to deploy five virtual machines to a virtual network subnet.
Each virtual machine will have a public IP address and a private IP address.
Each virtual machine requires the same inbound and outbound security rules.
What is the minimum number of network interfaces and network security groups that you require?

Box 1: 5
A public and a private IP address can be assigned to a single network interface.
By default a NIC is associated to one IP address. Anyway nothing prevents a NIC to have MORE THAN ONE IP address. So to the VM's NIC, you can associate the public and the private IP at the same time. You are not forced to have one NIC for the public IP and one NIC for the private IP.
Box 2: 1
You can associate zero, or one, network security group to each virtual network subnet and network interface in a virtual machine. The same network security group can be associated to as many subnets and network interfaces as you choose.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-network/virtual-network-network-interface-addresses
You have an Azure virtual network named VNet1 that connects to your on-premises network by using a site-to-site VPN. VNet1 contains one subnet named Subnet1.
Subnet1 is associated to a network security group (NSG) named NSG1. Subnet1 contains a basic internal load balancer named ILB1. ILB1 has three Azure virtual machines in the backend pool.
You need to collect data about the IP addresses that connects to ILB1. You must be able to run interactive queries from the Azure portal against the collected data.
What should you do?
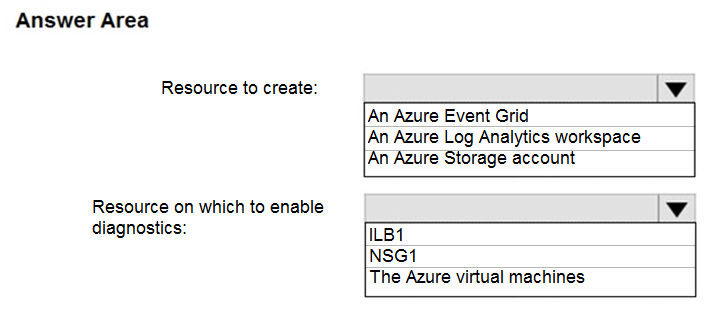
Box 1: An Azure Log Analytics workspace
In the Azure portal you can set up a Log Analytics workspace, which is a unique Log Analytics environment with its own data repository, data sources, and solutions.
Box 2: NSG1
NSG flow logs allow viewing information about ingress and egress IP traffic through a Network security group. Through this, the IP addresses that connect to the ILB can be monitored when the diagnostics are enabled on a Network Security Group.
We cannot enable diagnostics on an internal load balancer to check for the IP addresses.
As for Internal LB, it is basic one. Basic can only connect to storage account. Also, Basic LB has only activity logs, which doesn't include the connectivity workflow. So, we need to use NSG to meet the mentioned requirements.
Reference:
https://docs.microsoft.com/en-us/azure/log-analytics/log-analytics-quick-create-workspace
https://docs.microsoft.com/en-us/azure/load-balancer/load-balancer-standard-diagnostics